Continuous Security with Find-Sec-Bugs
One of the hardest software quality characteristic to cover in automated tests is security. In my Automated testing vs manual testing - security perspective blog I have mentioned that it’s almost impossible to rely solely on automation, especially in cases where human factor is involved (phishing, social engineering or plain ignorance).
It doesn’t change the fact that some aspects of security can, or even should be automated. The easiest starting point is dependencies. For Java projects, you can use OWASP Dependency Checker (see my blog postfor more details) and for npm projects consider using audit.
Certain vulnerabilities can be tested daily in the regression test suite. You can see here how to Automate your XSS tests with Selenium. The same tool can be used to test Unvalidated redirects. I’ll show how on my blog soon.
Today I’d like to present you a tool called Find Security Bugswhich detects 128 bug patternsjust by reading your Java code. The described tool can be used also as IntelliJ plugin, Sonar extension, but in this post, I’ll cover Maven integration.
Setup
Introducing find-sec-bugs plugin into your Maven projects is very simple. Here is the example configuration which you need to add into pom.xml file.
<build>
<plugins>
<plugin>
<groupId>com.github.spotbugs</groupId>
<artifactId>spotbugs-maven-plugin</artifactId>
<version>3.1.8</version>
<configuration>
<effort>Max</effort>
<threshold>Low</threshold>
<failOnError>true</failOnError>
<includeFilterFile>src/test/resources/spotbugs-security-include.xml
</includeFilterFile>
<excludeFilterFile>src/test/resources/spotbugs-security-exclude.xml
</excludeFilterFile>
<plugins>
<plugin>
<groupId>com.h3xstream.findsecbugs</groupId>
<artifactId>findsecbugs-plugin</artifactId>
<version>LATEST</version> <!-- Auto-update to the latest stable -->
<executions>
<execution>
<phase>package</phase>
<goals>
<goal>check</goal>
</goals>
</execution>
</executions>
</plugin>
</plugins>
</configuration>
</plugin>
</plugins>
</build>The configuration is quite long, so let’s explain few things. First of all, find-sec-bugs extends Maven extension which is available for quite some time - SpotBugs Maven Plugin. It’s a tool that reads your code and looks for bugs (bad practices, too complicated logic, code smells, etc).
Configuration values are explained on theextension page. The most useful is the failOnError flag which allows you to add described tool into Continuous Integration (CI) pipeline. If the analysis finds a security bug the build fails.
The Analysis can be narrowed down to scope which interests us. Here we focus only on security.
spotbugs-security-include.xml will look like this:
<FindBugsFilter>
<Match>
<Bug category="SECURITY"/>
</Match>
</FindBugsFilter>And spotbugs-security-exclude.xml will look like this:
<FindBugsFilter>
</FindBugsFilter>Finally, there is findsecbugs-plugin which we trigger in the following way:
a) CI purposes
mvn package -DskipTests=true findbugs:check
b) Verification purposes (human-readable report will be generated after triggering this command)
mvn findbugs:gui
As usual, I have added every piece of code into my Github project.
Demo
If you try to run mvn commands in my projects you won’t be able to observe anything interesting. The final report would be empty meaning there are no security vulnerabilities in analyzed code.
To observe find-sec-bugs in action let’s download OWASP WebGoatproject. It’s made insecure by design so we expect to find something this time.
Now do few things:
a) Run mvn clean install -DskipTests=true in whole WebGoat project
b) Go to cd webgoat-lessons/insecure-deserialization
c) Update pom.xml as mentioned in point 2.
d) Add spotbugs-security-include.xml and spotbugs-security-exlude.xml files to proper paths (they need to match pom.xml configuration)
e) Run mvn findbugs:gui
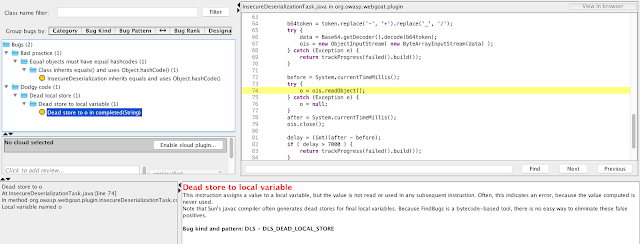
You should see report like this. As you can see the presented tool was able to find a bug in tested module.
Credits
The following blog post was inspired by Michał Kowalski TestWarez presentation. Thanks :)
Tags: security
Categories: Security
Updated:
